Wireless network pass on to any kind of computer network that is cable less and generally linked with a telecommunications and based on IEEE 802.11. Wireless Network can implement between nodes without any wire and remote information transmission system uses the radio waves, at the physical level of the network. There are several benefits of Wireless Network such as file sharing, Internet connection sharing, multi-player games, Internet telephone service, Computer mobility, and No unsightly wires. 802.11 support networking bandwidth and have an array of choices such as 802.11b, 802.11a,802.11g, 802.11n also known as Wi-Fi technologies and designed for precise networking programs. The hardware requirements of a Wireless network are Network adapter, Repeater, Network hub, and Modem.
There are different types of Wireless Networks such as LAN in which radio signals are used instead of wires and transmit data from one Pc to other Pc in the same network as it is Wi-Fi is a wireless network that enables connection to internet with WiFi functionality. it produced radio waves that can be picked up by WiFi receiver and fixed wireless data is also type of LAN that can be connect more then one building with the mean of sharing .The MAN have ability to connect several local area networks and a term WiMax used to represent wireless metropolitan area networks and Mobile devices networks contains Global System for Mobile Communications which is called GSM network and mainly used for cellular phones, Personal Communications Service is a radio band used to set up PCS and D-AMPS is an upgrade version of AMPS.
A Wireless network containing basic setup and to use a wireless network you have to need a networking card and Kernel config require IEEE 802.11 wireless network driver, Hardware Access Layer and ample Rate control algorithm. Wireless to crypto support modules .There are different kind of protocol used in a Wireless network, it has routing protocol such as DSDV, AODV, B.A.T.M.A.N, PWRP, DSR, OLSR, OORP, TORA,HSLS and The Ad-Hoc Configuration Protocol and Proactive Auto configuration. There are different related terms used for wireless network like WEP is a security protocol from IEEE, SSID, Static IP, DHCP, Subnet, LAN, WLAN, MAC, WAP, and Sniffer but the most commonly used term in these days is Wi-Fi such a technology wrapping the world.
Wireless network faces much security threat due to some reason as Spread spectrum used in LAN not very protected because the spreading codes openly therefore companies can intend the 802.11 mechanism and a hacker can easily demolish the security as it is a hacker can still snuffle the SSID. The use of DHCP in wireless network is also helpful for hacker to spoil your files because it automatically assigns IP addresses to users as they become active and hang the system. Generally networking security attack divided into two types which are passive and active .Passive including Eavesdropping, and Traffic analysis and active including Masquerading, Replay, Message modification, Denial-of-service. Loss if integrity and confident also cause of lack of security so it is necessary for all organizations that they make their system more secure even than before as no one can interrupt in it.
4G4G - fourth generation, is also known as `Beyond 3G`! 4G will offer a total evolution in wireless comms and will allow users to get voice, data and multimedia whenever they want it, wherever they are - and at far higher streaming or transfer rates than ever experienced before. It’s expected to be working commercially by 2015, as the 3G networks are anticipated by then to be fully congested.
It’s hard to quantify yet exactly what 4G is, or will be. However it’s expected that it will be entirely IP based, and will be able to provide speeds of a whopping 100Mbit/s - 1 Gigabits, absolutely anywhere - of the highest quality, and with superior security attached. It will be able to offer products and services never seen before, and hopefully at reasonable prices (previous phone based services have often been expensive.) Certainly though, 4G should be able to offer streamed HD television - with movie downloads at around 5 minutes - as well as improved MMS (multimedia messaging service), mobile TV - as well as HD-TV content and video chat - all delivered `anytime, anywhere.
No doubt there will be stringent international standards attached for 4G, in the same way that there were European ones attached to 2G. Currently, various companies are claiming that they’re already in possession of this new 4G technology, but some commentators feel that this is misleading, and simply serves to confuse customer and investors. It does seem however that 4G is being most successfully championed in Japan, and in fact the first 4G phones may start to appear shortly. For now it’s a `wait and see` as companies battle it out over who can successfully launch the first genuine and robust 4G products to market - and consumers may increasingly will bide their time, particularly as each generation evolution means entirely replacing the previous generation’s mobile devices!
Who knows how long it will be until the first whispers of 5G will start to emerge? Answers on a postcard please! There are numerous online resources which will allow you to discover more about emerging trends
Wi-FiWireless Fidelity – popularly known as Wi-Fi, developed on IEEE 802.11 standards, is the recent technology advancement in wireless communication. As the name indicates, WI-FI provides wireless access to applications and data across a radio network. WI-FI sets up numerous ways to build up a connection between the transmitter and the receiver such as DSSS, FHSS, IR – Infrared and OFDM. The development on WI-FI technology began in 1997 when the Institute of Electrical and Electronic Engineers (IEEE) introduced the 802.11 technology that carried higher capacities of data across the network. This greatly interested some of major brands across the globe such as the world famous Cisco Systems or 3COM. Initially, the price of Wi-Fi was very high but around in 2002, the IT market witnessed the arrival of a break through product that worked under the new 802.11 g standards. In 2003, IEEE sanctioned the standard and the world saw the creation of affordable Wi-Fi for the masses.
Wi-Fi provides its users with the liberty of connecting to the Internet from any place such as their home, office or a public place without the hassles of plugging in the wires. Wi-Fi is quicker than the conventional modem for accessing information over a large network. With the help of different amplifiers, the users can easily change their location without disruption in their network access. Wi-Fi devices are compliant with each other to grant efficient access of information to the user. Wi-Fi location where the users can connect to the wireless network is called a Wi-Fi hotspot. Through the Wi-Fi hotspot, the users can even enhance their home business as accessing information through Wi-Fi is simple. Accessing a wireless network through a hotspot in some cases is cost-free while in some it may carry additional charges. Many standard Wi-Fi devices such as PCI, miniPCI, USB, Cardbus and PC card, ExpressCard make the Wi-Fi experience convenient and pleasurable for the users. Distance from a wireless network can lessen the signal strength to quite an extent; some devices such as Ermanno Pietrosemoli and EsLaRed of Venezuela Distance are used for amplifying the signal strength of the network. These devices create an embedded system that corresponds with any other node on the Internet.
The market is flooded with various Wi-Fi software tools. Each of these tools is specifically designed for different types of networks, operating systems and usage type. For accessing multiple network platforms, Aircrack-ng is by far the best amongst its counterparts. The preferred Wi-Fi software tools list for Windows users is: KNSGEM II, NetStumbler, OmniPeek, Stumbverter, WiFi Hopper, APTools. Unix users should pick any of the following: Aircrack, Aircrack-ptw, AirSnort, CoWPAtty,Karma . Whereas, Mac users are presented with these options: MacStumble, KisMAC, Kismet. It is imperative for users to pick out a Wi-Fi software tool that is compatible with their computer and its dynamics.
Wi-Fi uses radio networks to transmit data between its users. Such networks are made up of cells that provide coverage across the network. The more the number of cells, the greater and stronger is the coverage on the radio network. The radio technology is a complete package deal as it offers a safe and consistent connectivity. Radio bands such as 2.4GHz and 5GHz depend on wireless hardware such Ethernet protocol and CSMA. Initially, Phase Shift Keying (PSK), a modulation method for conveying data was used, however now it has been replaced with CCK. Wi-Fi uses many spectrums such as FHSS and DSSS. The most popular Wi-Fi technology such as 802.11b operates on the range of 2.40 GHz up to 2.4835 GHz band. This provides a comprehensive platform for operating Bluetooth strategy, cellular phones, and other scientific equipments. While 802.11a technology has the range of 5.725 GHz to 5.850 GHz and provides up to 54 Mbps in speed. 802.11g technology is even better as it covers three non-overlapping channels and allows PBCC. 802.11e technology takes a fair lead by providing excellent streaming quality of video, audio, voice channels etc.
To connect to a Wi-Fi network an adapter card is essential. Additional knowledge about the SSID, infrastructure, and data encryption is also required. The Wi-Fi users don’t have to be concerned with the security issues. The security methods such as MAC ID filtering

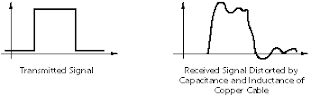 These effects are properties of transmission through metallic conductors, and become more pronounced as the conductor length increases. To compensate for distortion, signal power must be increased or the transmission rate decreased.
These effects are properties of transmission through metallic conductors, and become more pronounced as the conductor length increases. To compensate for distortion, signal power must be increased or the transmission rate decreased.


